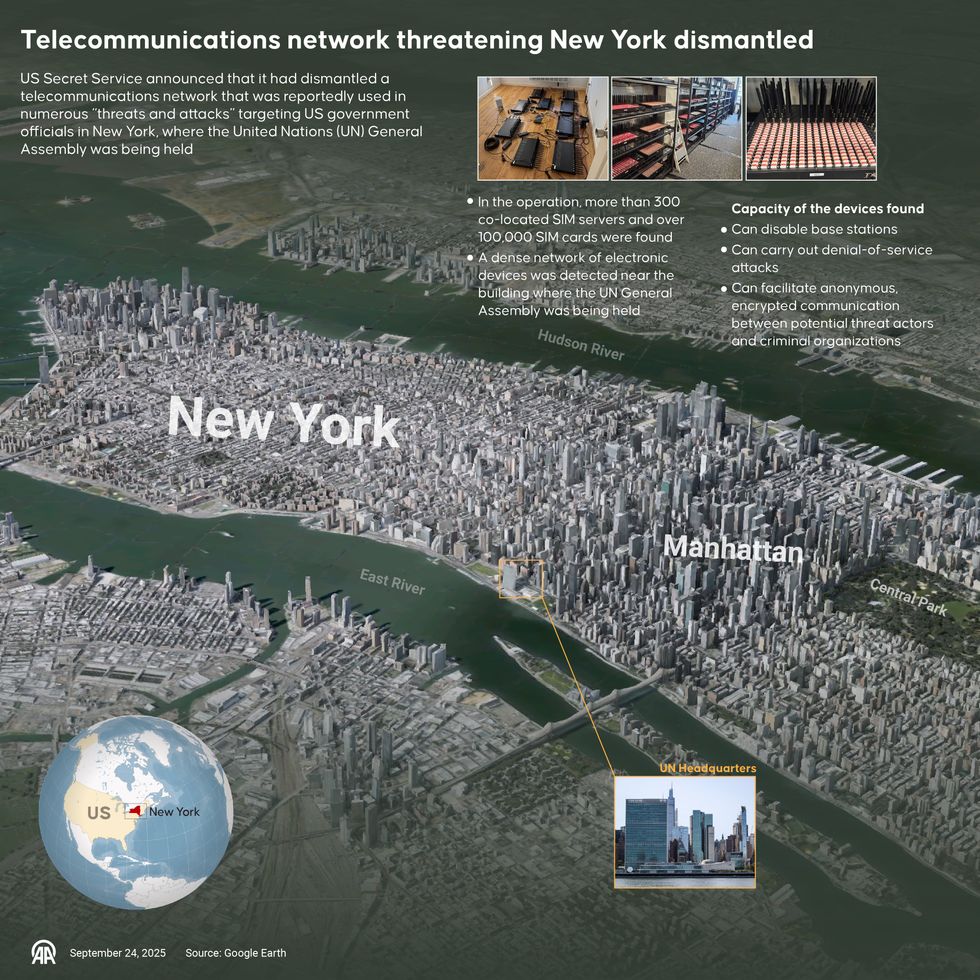
The gadgets had been designed to create what consultants name a “SIM farm,” an industrial-scale operation the place tons of or 1000’s of SIM playing cards could be manipulated concurrently. These setups are usually related to monetary fraud or bulk messaging scams. Nonetheless, the Secret Service warned that they will also be used to flood telecom networks, disable cell towers, and obscure the origin of communications.
Within the shadow of the UN, the place world leaders convene and safety tensions are excessive, the proximity of such a system raised quick questions on intent, attribution, and preparedness.
“(SIM farms) might jam cell and textual content providers, block emergency calls, goal first responders with pretend messages, unfold disinformation, or steal login codes,” Jake Braun, Govt Director of the Cyber Coverage Initiative on the College of Chicago and former White Home Performing Principal Deputy Nationwide Cyber Director, tells The Cipher Temporary. “Briefly, they may cripple communications simply after they’re wanted most.”
Join the Cyber Initiatives Group Sunday publication, delivering expert-level insights on the cyber and tech tales of the day – on to your inbox. Join the CIG publication right this moment.
How SIM Farms Work
At their core, SIM farms exploit the basic structure of cell networks. Every SIM card represents a novel identification on the worldwide communications grid. By biking by SIMs at excessive velocity, operators can generate large volumes of calls, texts, or information requests that overwhelm mobile infrastructure. Such floods can mimic the results of a distributed denial-of-service (DDoS) assault, besides the assault comes by authentic service channels relatively than apparent malicious visitors.
“SIM farms are primarily racks of modems that cycle by 1000’s of SIM playing cards,” Dave Chronister, CEO of Parameter Safety, tells The Cipher Temporary. “Operators continually swap SIM playing cards and system identifiers so visitors seems unfold out relatively than coming from a single supply.”
That makes them extraordinarily troublesome to detect.
“They will mimic authentic enterprise texts and calls, conceal behind residential web connections, or scatter gear throughout atypical areas so there’s no single, apparent sign to flag,” Chronister continued. “As a result of SIM farms make it laborious to tie a quantity again to an actual particular person, they’re helpful to drug cartels, human-trafficking rings and different organized crime, and the identical concealment options may be enticing to terrorists.”
That potential to mix in, consultants spotlight, is what makes SIM farms greater than only a prison nuisance.
Whereas SIM farms could initially be used for monetary fraud, their structure could be simply repurposed for coordinated cyber-physical assaults. That dual-use nature makes them particularly interesting to each transnational prison teams and state-backed intelligence providers.
Who May Be Behind It?
The Secret Service, nevertheless, has not publicly attributed the community close to the UN to any particular particular person or entity. Investigators are weighing a number of prospects: a transnational fraud ring exploiting the chaos of UN week to run large-scale scams, or a extra regarding state of affairs the place a state-backed group positioned the SIM farm as a contingency device for disrupting communications in New York.
Officers famous that the operation’s sophistication prompt it was not a low-level prison endeavor. The {hardware} was able to sustained operations in opposition to a number of carriers, and its sheer scale — 100,000 SIM playing cards — far exceeded the everyday scale of fraud schemes. That raised the specter of hostile governments probing U.S. vulnerabilities forward of potential hybrid battle situations.
Analysts notice that Russia, China, and Iran have all been implicated in mixing prison infrastructure with state-directed cyber operations. But, these setups serve each criminals and nation-states, and attribution requires extra particulars than are publicly out there.
“Legal teams use SIM farms to become profitable with scams and spam,” mentioned Braun. “State actors can use them on a much bigger scale to spy, unfold disinformation, or disrupt communications — and typically they piggyback on prison networks.”
One supply within the U.S. intelligence neighborhood, who spoke on background, described that overlap as “hybrid infrastructure by design.”
“It could possibly sit dormant as a prison enterprise for years till a international authorities wants it. That’s what makes it so insidious,” the supply tells The Cipher Temporary.
From Chronister’s purview, the “possible clarification is that it’s a classy prison enterprise.”
“SIM-farm infrastructure is often run for revenue and could be rented or resold. Nevertheless, the prison ecosystem is fluid: nation-states, terrorist teams, or hybrid actors can and do co-opt prison capabilities when it fits them, and a few state-linked teams domesticate shut ties with prison networks,” he mentioned.
The Broader Nationwide Safety Blind Spot
The incident through the United Nations Common Meeting additionally underscores a rising blind spot in U.S. protecting intelligence: telecommunications networks as contested terrain. For many years, federal sources have targeted closely on cybersecurity, counterterrorism, and bodily threats. On the similar time, the connective tissue of recent communications has typically been handled as a business area, monitored by carriers relatively than safety companies.
The Midtown bust means that assumption not holds. The Secret Service itself framed the incident as a wake-up name.
“The potential for disruption to our nation’s telecommunications posed by this community of gadgets can’t be overstated,” acknowledged U.S. Secret Service Director Sean Curran. “The U.S. Secret Service’s protecting mission is all about prevention, and this investigation makes it clear to potential dangerous actors that imminent threats to our protectees shall be instantly investigated, tracked down and dismantled.”
Nevertheless, consultants warn that U.S. defenses stay fragmented. Carriers give attention to fraud prevention, intelligence companies monitor international adversaries, and regulation enforcement investigates home crime. The seams between these missions are exactly the place SIM farms thrive.
The Cipher Temporary brings expert-level context to nationwide and world safety tales. It’s by no means been extra essential to grasp what’s occurring on the planet. Improve your entry to unique content material by changing into a subscriber.
Hybrid Warfare and the Subsequent Entrance Line
The rise of SIM farms displays the evolution of hybrid warfare, the place the boundary between prison exercise and state motion blurs, and adversaries exploit business infrastructure as a way of assault. Simply as ransomware gangs can moonlight as proxies for hostile intelligence providers, telecom fraud networks could double as latent disruption instruments for international adversaries.
Moreover, the menace mirrors patterns noticed overseas. In Ukraine, officers have reported Russian operations focusing on mobile networks to disrupt battlefield communications and sow panic amongst civilians. In components of Africa and Southeast Asia, SIM farms have been linked to each organized crime syndicates and intelligence-linked affect campaigns.
That very same playbook, consultants warning, might be devastating if utilized within the coronary heart of a worldwide metropolis.
“If activated throughout a disaster, such networks might flood cellphone strains, together with 911 and embassy hotlines, to sow confusion and delay coordination. They will additionally blast pretend alerts or disinformation to set off panic or misdirect first responders, making it a lot more durable for authorities to handle an already unstable scenario,” Chronister mentioned. “As a result of these setups are comparatively low-cost and scalable, they’re a cheap however efficient technique to complicate emergency response, authorities decision-making, and even protecting particulars.”
Wanting Forward
The dismantling of the clandestine telecom community in New York could have prevented an imminent disaster, however consultants warning that it’s unlikely to be the final of its variety. SIM farms are cheap to arrange, scalable throughout borders, and sometimes hidden in plain sight. They characterize a convergence of cyber, prison, and nationwide safety threats that the U.S. is just starting to deal with as a unified problem.
In relation to what must be performed subsequent, Braun emphasised the significance of “bettering data sharing between carriers and authorities, investing in higher instruments to identify hidden farms, and shifting away from SMS for delicate logins.”
“Deal with SIM farms as a nationwide safety menace, not simply telecom fraud. Restrict entry to SIM farm {hardware} and punish abuse. Assist smaller carriers strengthen defenses,” he continued. “And streamline authorized steps so takedowns occur sooner.”
Chronister acknowledged that whereas “carriers are significantly better than they had been 5 or ten years in the past, as they’ve invested in spam filtering and fraud analytics, attackers can nonetheless get by after they rotate SIMs shortly, use eSIM provisioning, or unfold exercise throughout jurisdictions.”
“Legislation enforcement and intelligence have highly effective instruments, however authorized, technical, and cross-border constraints imply detection typically outpaces assured attribution and speedy takedown. Make it more durable to purchase and cycle by SIMs in bulk and strengthen identification verification for cellphone numbers,” he added. “Require sooner, real-time information-sharing between carriers and authorities throughout visitors spikes, enhance authentication for public alerts, and run common stress-tests and red-team workout routines in opposition to telecom infrastructure. Lastly, construct joint takedown and mutual-assistance preparations with allies so attackers can’t merely reconstitute operations overseas.”
Are you Subscribed to The Cipher Temporary’s Digital Channel on YouTube? There isn’t any higher place to get clear views from deeply skilled nationwide safety consultants.
Learn extra expert-driven nationwide safety insights, perspective and evaluation in The Cipher Temporary as a result of Nationwide Safety is Everybody’s Enterprise.